部落格
主頁 » 部落格
IDC LINK: Raritan’s new iPDU is a Building Block for Smarter Datacenters
Posted on April 18, 2017 by Gento

The industry can’t stop talking about Raritan’s new portfolio of intelligent power products equipped with the advance iX7 controller. According to IDC research “As organizations utilize more edge datacenter resources to support digital transformation and IoT initiatives, the ability to remotely manage and control datacenter infrastructure will become a must-have feature. Infrastructure such as Raritan's iX7-powered iPDUs will be an integral building block for smarter datacenters.”
How Secure are Raritan’s PX Intelligent PDUs?
Posted on April 10, 2017 by Gento

Why is security so important in data centers? Well, according to the 2016 Ponemon Cost of Data Breach Study the average cost of an information security breach is $4 million, with an average estimated cost of $154 per stolen record. Raritan believes that if a device is on a network, it has to have a set of security measures in place to protect the device, its data and the network it is connected to.
Top 10 Reasons Why Hardware Intelligence is Critical for Your Data Center Rack
Posted on April 5, 2017 by Gento

Your data center is an absolutely critical part of the business. In fact, the data center of today has evolved into an entity which is tasked with handling more services than ever before. Today, we are seeing entire platforms and new services being born directly within cloud-ready data center platforms.
What Is the iX7™ Advance PDU Controller and How Could It Improve My Data Center Operations?
Posted on April 4, 2017 by Gento
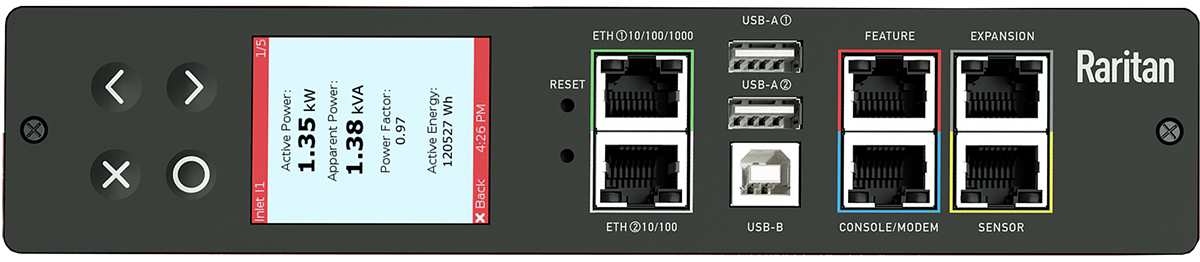
The iX7™ intelligent controller is Raritan’s newest advancement in the PDU industry. Before going into the details of what the iX7™ encompasses and why it’s changing the industry, it’s important to know the basic components of an intelligent PDU to help further your understanding.
Data Center Cabinet Load Balancing: there’s a less complicated way.
Posted on March 28, 2017 by Gento
Why do we load balance?
Without going into the complicated math, suffice it to say that load balancing in a 3 phase system is desirable. The more unbalanced a system the more problems it creates. UPS life, for one, can be affected by unbalanced systems. Although one circuit (server cabinet) being out of balance won’t have much effect, if many or all circuits on a panel are out of balance, the main circuit supplying the breaker panel will be out of balance and this can ruin your upstream UPS. There are also efficiency issues with unbalanced loads.
How is load balancing currently accomplished in a rack cabinet?
To balance a load in a cabinet, the loads of the equipment power supplies are spread across the 3 phases – L1/L2, L2/L3, L3/L1. This is done by plugging the first server (or switch/router) in an outlet wired on L1/L2, the next server on L2/L3, the next on L3/L1, then start over. The goal is to get an equal number of devices/loads on all 3 phases – or as close as possible.
This approach can quickly turn into a cabling nightmare. Most rack PDUs are linear in their phase layout of outlets – there are only three banks of outlets, one for each phase. For example, on a 36 outlet PDU, outlets 1 through 12 will be on L1/L2, 13 through 24 on L2/L3, and 25 through 36 on L3/L1. If you use the above method of balancing, and start racking the devices at the bottom U position, the third device you plug in will need to reach the top third of the PDU and the last device may have to reach back to the bottom of the PDU. In other words, a lot of crisscrossed cabling.
How do Raritan’s balance the cable and load balancing challenge?
In certain Raritan PX three-phase models the architecture gets around the cabling issue by staggering the grouping of outlets - there are at least 6 banks of outlets. For example, outlets 1 through 6 are on L1/L2, 7 through 12 on L2/L3, 13 through 18 on L3/L1, but then we start over at L1/L2 for outlets 19 through 24. (See Illustration below)
This intelligently engineered architecture results in more reliability and easier execution. The devices towards the top of the cabinet don’t need to be plugged in to the bottom of the PDU and devices at the bottom don’t need to be plugged in to the top.
訂閱
近期活動
- New Zealand Cloud & Datacenter Convention 2022
- 3 November 2022, 9am – 4pm • Grand Millennium Hotel, Auckland, New Zealand
- Data Centre World Singapore
- 12th – 13th Oct 2022
- Korea Cloud & Datacenter Convention 2022
- 6th Oct 2022
- Philippines Cloud & Datacenter Convention 2022
- 4th Aug 2022
- JANOG50 Meeting Hokkaido
- 3th – 15th July 2022
Raritan最新新聞
- Legrand 使用兩大創新智慧型機架 PDU 重新活化資料中心產業
- Posted on May 1, 2023
- Exclusive interview丨How does Huizhou upgrade its manufacturing industry?
- Posted on December 2, 2021
- Raritan 發表 MasterConsole® 數位雙電腦切換器
- Posted on February 18, 2021
- Legrand Data, Power and Control Division Announced as Finalist in Six Categories at DCS Awards 2020
- Posted on November 9, 2020
- Raritan 新款智慧機櫃控制器 (SRC) 可智慧管理資料中心與關鍵任務設施的環境與安全性資訊
- Posted on November 9, 2020